Don't be the next victim of a cyberattack.
Businesses are more vulnerable than ever: Ransomware attacks, data leaks, unauthorized access, and system downtime are real risks! And they are increasingly scalable as hackers use AI to develop mass attacks.
If you think you are safe, you are wrong!

It only takes one click on the wrong email, one forgotten update, or one off-hours access to put your entire business at risk.
Did you know that...
- 95% of companies suffer breaches due to human error?
(source: Infosecurity Magazine) - 62% of all cyberattacks target SMEs? For hackers, you are not "too small," but "the easiest target."
(source: IBM/Astra Security) - 60% of SMEs that suffer an attack go out of business in less than six months.
(source: NCSA/Cybersecurity Ventures) - 54% of security failures are fixed in time?
(source: Verizon Databreach Report)

Zamak protects what sustains your business:
Without scheduled routines, strong preventive automations, continuous monitoring, periodic management reports, and constant team training, any tool becomes a false sense of security.
With Zamak, your company adopts a preventive, automated, centralized approach on our unified and auditable management platform. You also have access to an experienced multidisciplinary team that is constantly training, as well as training for your team. We protect not only data and systems but also your entire operation, your money, and your reputation.Our squad of defense AIs and trained team by your side,every day!
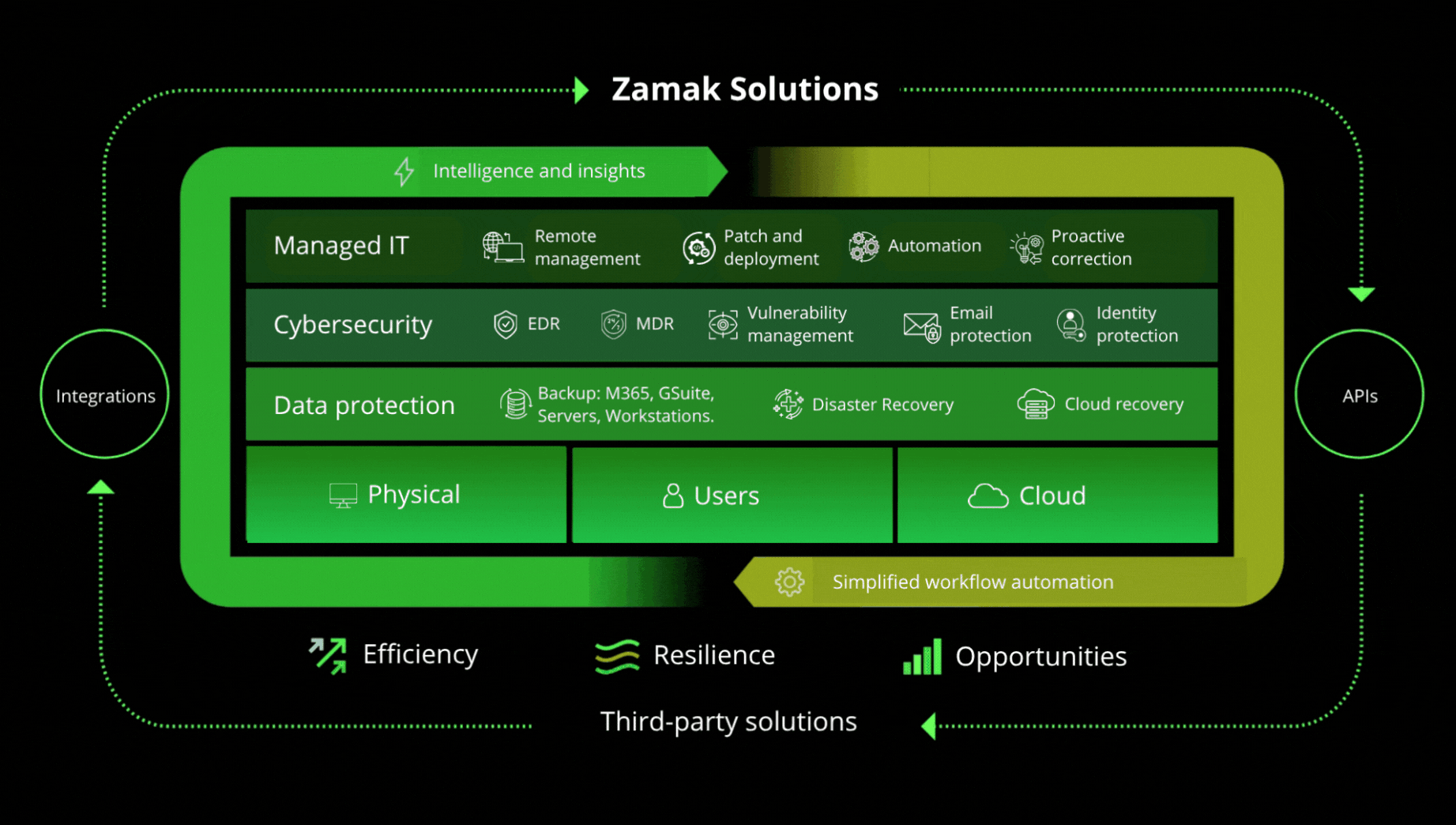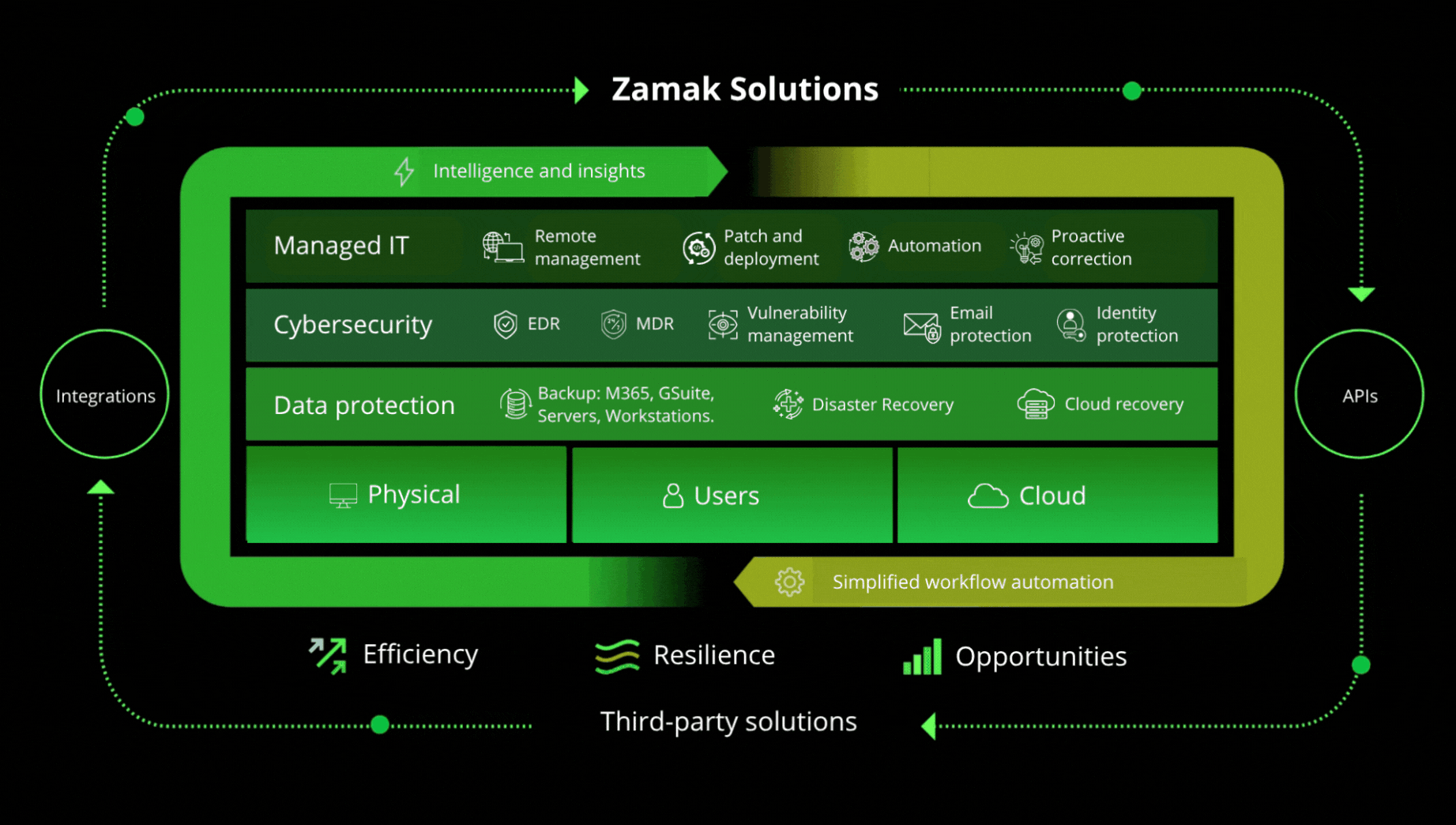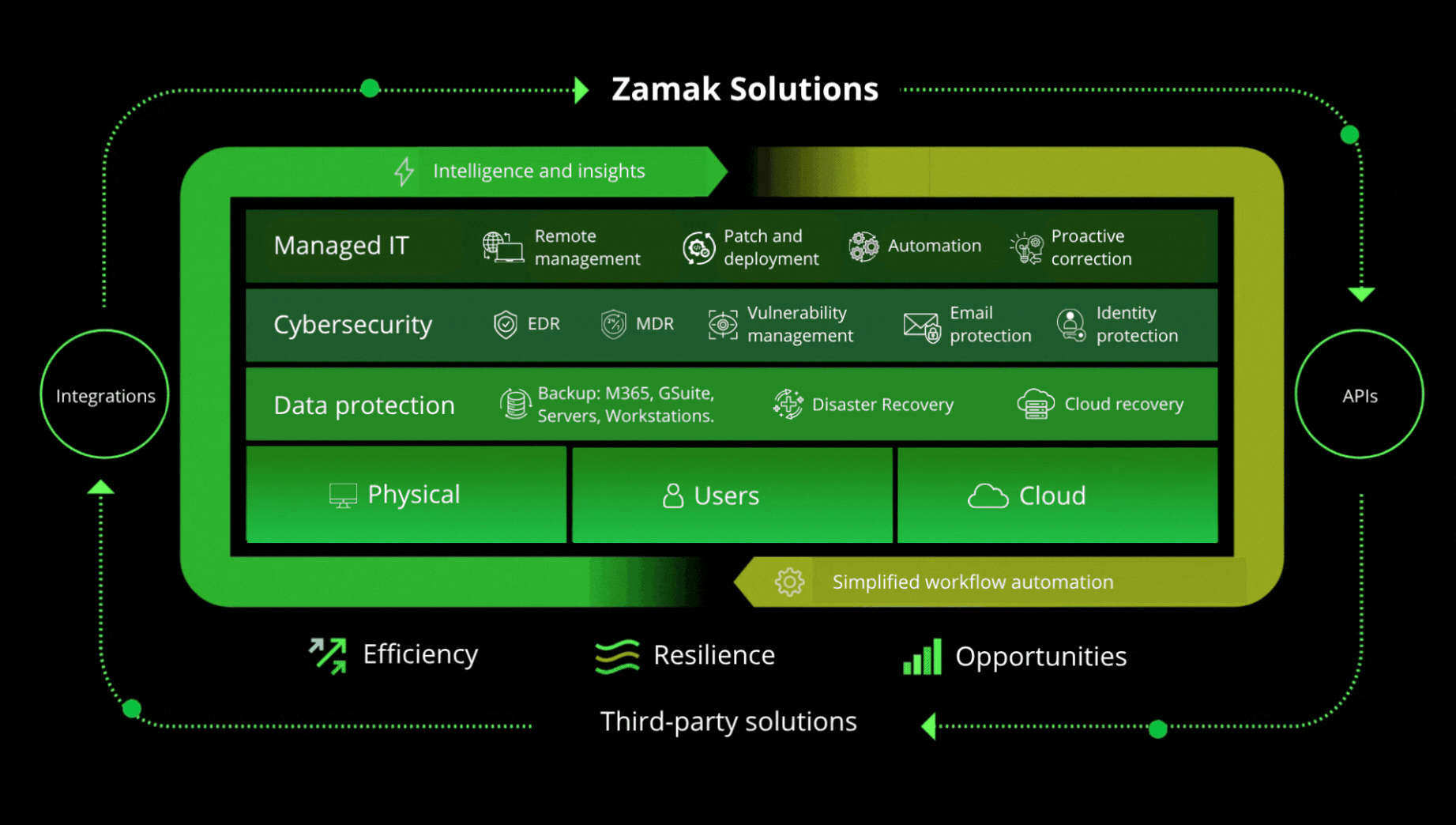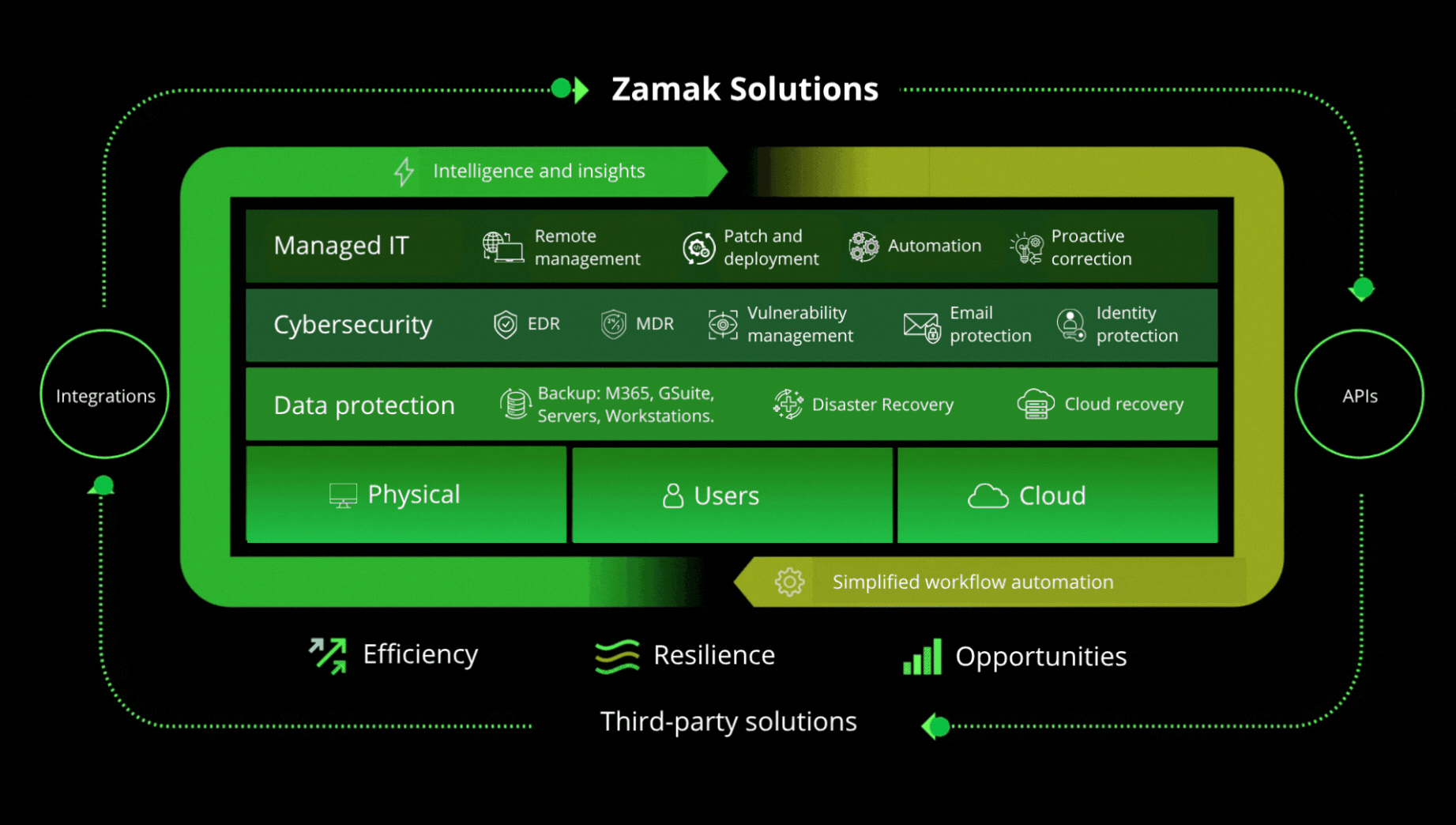
Endpoints Shielding
Next-generation shielding with active AI protection against ransomware and new threats for desktops, laptops, and servers, neutralizing emerging threats in real time, isolating and eradicating attacks before they cause network damage.
Web and Email Protection
Intelligent traffic filters with blocks for sensitive data capture, malicious links, phishing, dangerous attachments, and content non-compliant with company policies. All for continuous protection of corporate browsing and emails.
Intelligent Update Management
Intelligent and proactive management of automated application of critical updates to systems and software, reducing vulnerabilities exploitable by cybercriminals. Every computer has a multitude of software and HW drivers that require daily fixes.
Secure Backup and Disaster Recovery
Protection against data loss and digital hijacking. We guarantee the inviolability of your stored data and the ability to perform a complete restoration of operations in minutes, not days, preventing you from becoming part of the statistic of companies that close after an attack.
Vulnerability Management and Penetration Testing
We don't wait for a breach to happen; we look for it! Our specialists conduct periodic vulnerability assessments and simulate controlled Penetration Tests (Pentests). This proactive approach identifies weaknesses in the network, infrastructure, and applications before a hacker does.
Compliance, Governance, and Anti-Fraud Training
Your team is your frontline and requires continuous training. Simultaneously, we implement compliance for all your IT practices and policies with global regulations (LGPD, HIPAA, ISO 27001, etc.), protecting your company against fines and reputational damage.